Bug Type: Stored XSS Vulnerability | Self Executed
Vulnerable parameter: Playlist Name
Status : Fixed
Detailed WriteUp: Hey all 🙂 , Last month i reported a Stored XSS vulnerability to Google which was in youtube playlist module. The playlist name was not being sanitized properly which caused js code to be executed in few parts of site
Reproduction Steps :
1. Create a playlist name [ t” onmouseover=alert(/xss/); a=” ] . * Without rectangle braces [ ] .
2. Now there are multiple places where this above js code will execute . One is Click edit on any of your uploaded video . On editor page click on Add to Playlist . When you mouseover the playlist name the above js code will execute. Other place where the code gets executed is when we are uploading a video , there it ask for Add to playlist.
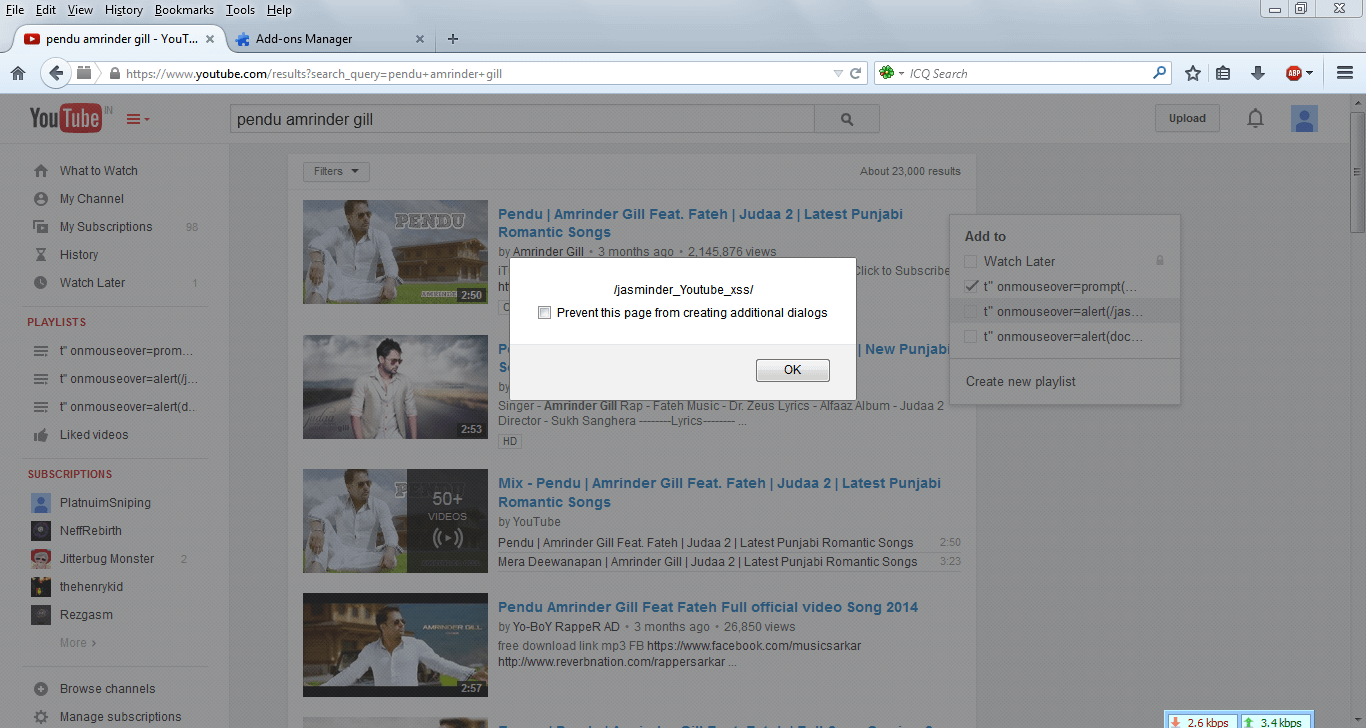
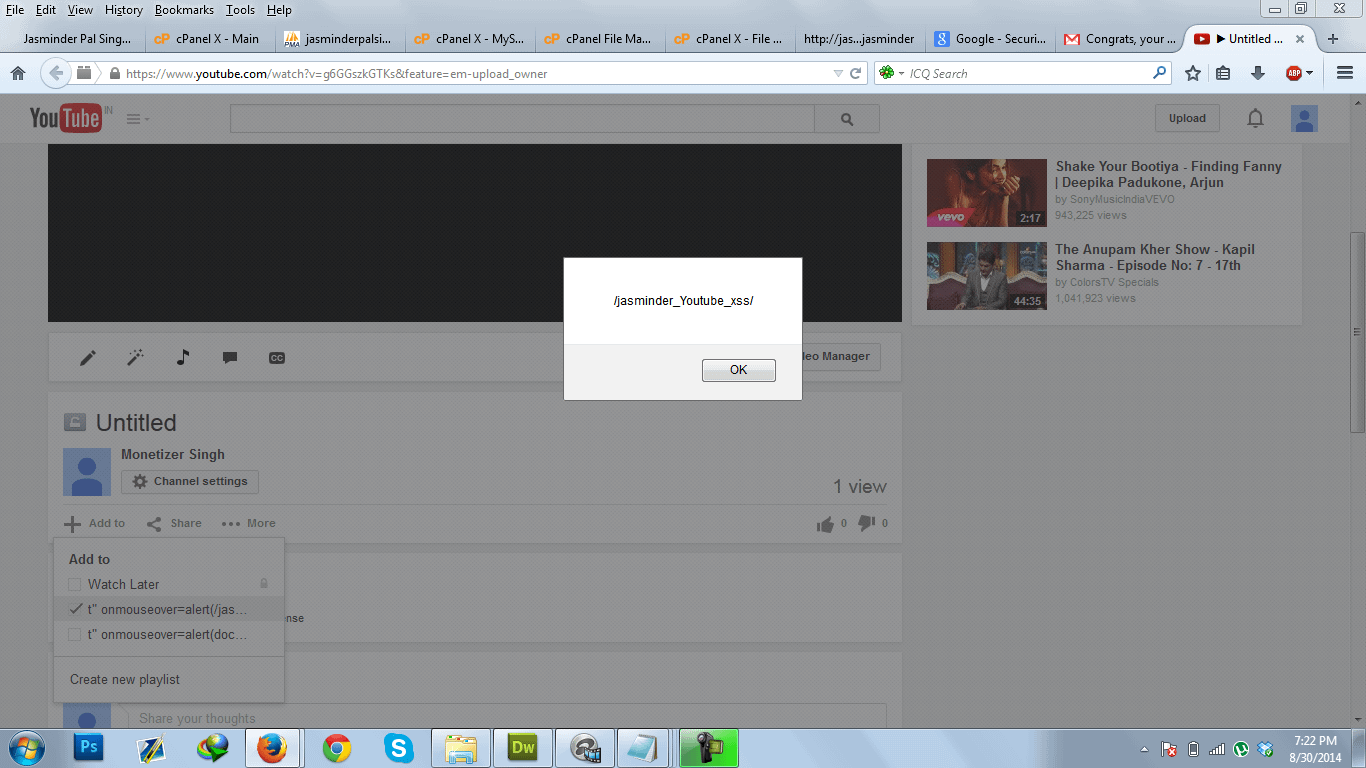 Thanks Google for the reward :
Thanks Google for the reward :
 On October 4 i reported another XSS in youtube. Will blog about that after fix.
On October 4 i reported another XSS in youtube. Will blog about that after fix.
Thanks for reading 🙂



