Bug Type: Stored XSS Vulnerability
Browser: Internet Explorer 7 or less
Vulnerable Module: Markup Helper : https://www.google.com/webmasters/markup-helper/
Status :Wont Fix .
Detailed WriteUp: Hey all 🙂 Back in December 2014 I reported a Cross Site Scripting vulnerability to Google Security . Google webmaster has a module of Structured Data Markup Helper which takes a website URL as a input and render it after blacklisting all the javascript calls or codes anywhere in the code . Tried some classical tricks to get some javascript code whitelisted but none worked. Rendered external url shows up in a iframe .
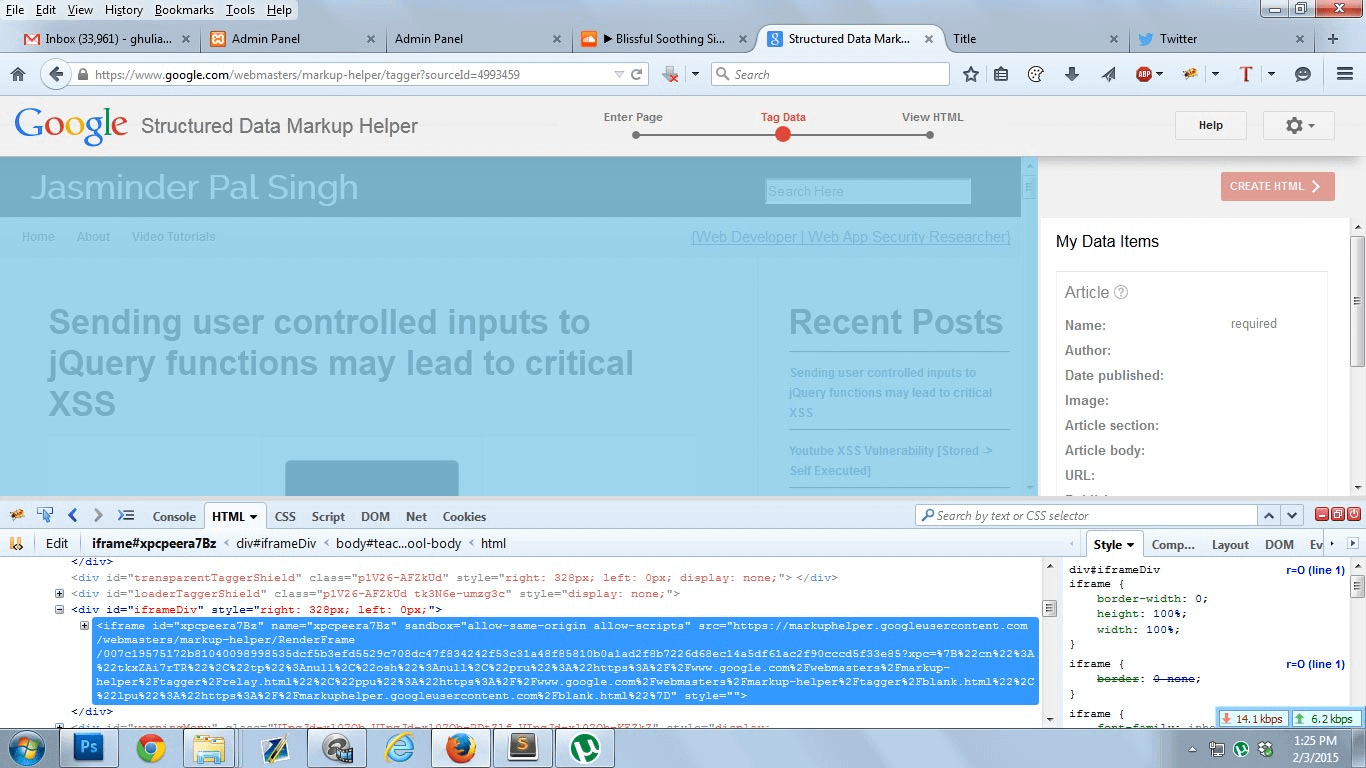 The actual web application code is being hosted on .
The actual web application code is being hosted on .
[pastacode lang=”markup” manual=”https%3A%2F%2Fmarkuphelper.googleusercontent.com%2F%0A” message=”” highlight=”” provider=”manual”/]
After giving up with attribute based javascripts events, i checked if style attribute is sanitized properly , fortunately it was not . I was able to inject javascript expressions in style attribute. So , i put the below vector in footer of my website code :
[pastacode lang=”markup” manual=”%3Cdiv%20style%3D%22width%3A%20expression(alert(%2FXSS_Jasminder%2F))%3B%22%3E%3C%2Fdiv%3E%0A” message=”” highlight=”” provider=”manual”/]
The javascript expressions is no more supported in modern browsers but till Internet Explorer 7 . After rendering nothing was ripped off from the vector as expected.
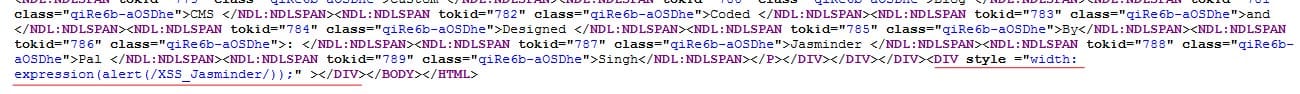
Now lets open the iframe src url in Internet Explorer 7 . The stored XSS payload gets fired.





